How HTTPS Works
Pass Any Cisco Exam On Your First Try.
Want to boot your networking career ? This is the chance for you.
How HTTPS Works: A Detailed Explanation
Introduction
Hypertext Transfer Protocol Secure (HTTPS) is the secure version of HTTP, the foundational protocol for transferring data on the web. HTTPS ensures that communication between a user's browser and a website is encrypted and secure, protecting data integrity and user privacy. This technology has become the standard for safeguarding online communications, e-commerce transactions, and sensitive information like passwords and credit card details.
Here, we’ll break down how HTTPS works, covering key concepts such as encryption, authentication, the role of certificates, and the underlying mechanisms that ensure security.
1. The Basics of HTTPS
HTTP operates as a plaintext protocol, meaning the data transferred between the client (browser) and server can be intercepted and read by third parties. HTTPS mitigates these risks by adding a layer of encryption and authentication through the use of Transport Layer Security (TLS).
Key Goals of HTTPS:
Encryption: Prevents eavesdropping by ensuring that data is unintelligible to anyone who intercepts it.
Authentication: Verifies the identity of the website to ensure users are connecting to the legitimate server.
Data Integrity: Protects data from being altered or tampered with during transmission.
2. The Role of TLS in HTTPS
TLS (Transport Layer Security), formerly known as SSL (Secure Sockets Layer), is the protocol that underpins HTTPS. It provides the mechanisms for secure communication, including encryption, key exchange, and authentication.
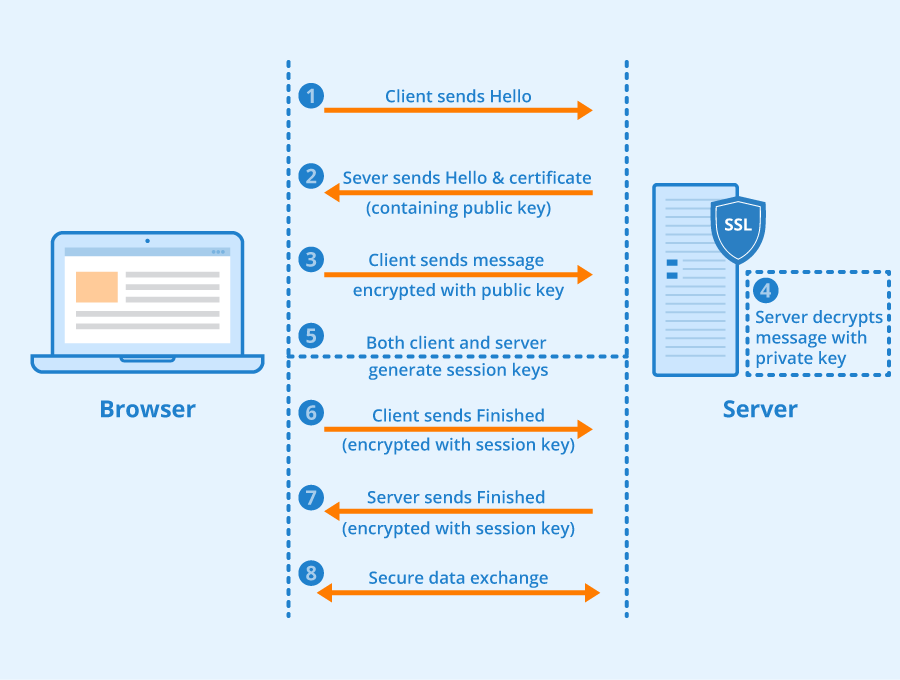
3. How HTTPS Works: Step-by-Step
Here’s a detailed breakdown of what happens when a user connects to a website over HTTPS:
1. Client Initiates Connection
The process begins when the user’s browser requests a secure connection to a website (e.g., by typing
https://example.com
).
This triggers the TLS Handshake.
2. Server Responds with Its Certificate
The server sends a digital certificate (commonly an X.509 certificate) issued by a trusted Certificate Authority (CA).
This certificate contains:
The server's public key.
The domain name the certificate is valid for.
The issuing CA’s details.
The certificate's expiration date.
A digital signature from the CA to verify authenticity.
3. Browser Verifies the Certificate
The browser checks the certificate to ensure:
It’s issued by a trusted CA.
It hasn’t expired.
It matches the domain name of the website.
If the certificate passes these checks, the handshake continues. Otherwise, the browser displays a warning.
4. Key Exchange and Session Establishment
Using the server’s public key from the certificate, the browser and server perform a key exchange to agree on a shared secret.
Depending on the TLS version:
Older TLS (RSA-based): The browser encrypts a session key using the server's public key and sends it back.
Modern TLS (Diffie-Hellman): Both parties independently generate the shared secret without directly transmitting it, making interception nearly impossible.
5. Symmetric Encryption
Once the session key is established, both the browser and server switch to symmetric encryption. This means the same key is used for both encrypting and decrypting data.
Symmetric encryption algorithms (e.g., AES) are fast and efficient, ensuring secure data transfer without significant performance overhead.
6. Data Transmission
All subsequent data is encrypted using the session key.
This encryption protects the confidentiality and integrity of the data being transferred.
7. Session Termination
When the session ends (e.g., the user closes the browser or navigates away), the session keys are discarded, ensuring no further data can be encrypted or decrypted with them.
4. Key Components of HTTPS
To fully understand HTTPS, let’s dive deeper into its critical components:
A. Public Key Infrastructure (PKI)
HTTPS relies on PKI, which involves:
Public and Private Keys: Asymmetric encryption uses a key pair:
Public Key: Shared openly and used for encryption.
Private Key: Kept secret and used for decryption.
Certificate Authorities (CAs):
Trusted entities that issue digital certificates to verify the identity of websites.
B. Encryption Algorithms
HTTPS employs various encryption algorithms:
Symmetric Algorithms: AES (Advanced Encryption Standard).
Asymmetric Algorithms: RSA, ECDSA (Elliptic Curve Digital Signature Algorithm).
Hashing: Used for data integrity (e.g., SHA-256).
C. TLS Handshake Protocol
The TLS handshake ensures secure communication. Modern versions (TLS 1.3) streamline this process to improve performance and security.
5. Benefits of HTTPS
Enhanced Privacy and Security: Prevents eavesdropping and data theft.
Search Engine Optimization (SEO): Search engines prioritize HTTPS-enabled sites.
User Trust: Browsers mark HTTPS sites as secure, increasing user confidence.
Compliance: Essential for adhering to data protection laws (e.g., GDPR).
6. Challenges and Misconceptions
A. HTTPS Does Not Guarantee Safety
HTTPS ensures a secure connection but doesn’t guarantee the legitimacy of the content. A phishing site can use HTTPS.
B. Performance Overheads
Modern HTTPS implementations minimize performance impacts, but encryption can slightly increase server load.
C. Certificate Management
Certificates need regular renewal and proper management to avoid downtime.
7. Evolving Standards
TLS has evolved to address vulnerabilities:
TLS 1.2: Widely used with strong encryption.
TLS 1.3: Simplifies the handshake and improves speed and security. Older versions like TLS 1.0/1.1 are deprecated due to vulnerabilities.
8. Tools for HTTPS Implementation
Let’s Encrypt: Provides free TLS certificates.
SSL Labs: Tests and grades HTTPS implementations.
Content Delivery Networks (CDNs): Simplify HTTPS adoption for large-scale deployments.
9. Real-World Use Cases
Banking: Protects financial transactions.
Healthcare: Secures patient data.
E-Commerce: Encrypts payment details.