How Does SNMP Work
Pass Any Cisco Exam On Your First Try.
Want to boot your networking career ? This is the chance for you.
Introduction to SNMP
Simple Network Management Protocol (SNMP) is an Internet Standard protocol for collecting and organizing information about managed devices on IP networks and for modifying that information to change device behavior. SNMP is widely used in network management for network monitoring. Devices that typically support SNMP include routers, switches, servers, workstations, printers, modem racks, and more.
Historical Context
SNMP was developed in the late 1980s as part of the Internet Protocol Suite (TCP/IP). The original version, SNMPv1, was introduced in 1988 and has since undergone several revisions, leading to SNMPv2c, SNMPv2u, SNMPv3, and beyond. Each version introduced enhancements in security, performance, and flexibility.
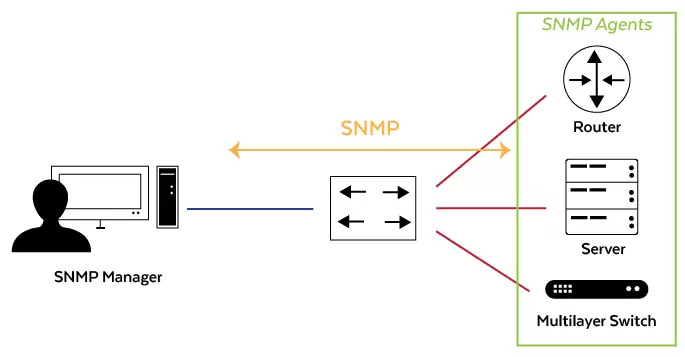
Basic Components of SNMP
SNMP operates with three key components:
Managed Devices: These are network nodes containing SNMP agents. They collect and store management information, making it available via SNMP.
Agents: These are software modules within the managed devices. An agent has local knowledge of management information and translates that information into an SNMP-compatible format.
Network Management Systems (NMS): These are applications that monitor and control managed devices. An NMS executes applications that monitor and control managed devices. They provide the bulk of the processing and memory resources required for network management.
SNMP Architecture
The architecture of SNMP consists of several layers:
Application Layer: This layer includes the SNMP protocol itself.
Transport Layer: This layer typically utilizes UDP (User Datagram Protocol) for communication.
Internet Layer: This layer involves IP (Internet Protocol) for routing the SNMP messages.
Network Access Layer: This is responsible for placing the SNMP messages onto the network medium.
SNMP Operations
SNMP works through a set of operations, defined by the protocol, that enable NMS to perform various tasks:
GET Operation: This operation is used by the NMS to retrieve the value of one or more variables from the managed device.
SET Operation: This operation allows the NMS to set the value of one or more variables on the managed device, thereby changing the configuration or behavior of the device.
GETNEXT Operation: This operation is used to retrieve the next variable in the Management Information Base (MIB) tree. It's used for traversing the MIB.
GETBULK Operation: Introduced in SNMPv2, this operation is used to efficiently retrieve large blocks of data from the managed devices.
TRAP Operation: This is a notification from the agent to the NMS indicating that an event has occurred. It's an unsolicited message, meaning it is sent without a request from the NMS.
INFORM Operation: Similar to TRAP, but it includes an acknowledgment from the NMS that the notification has been received.
RESPONSE Operation: This operation is used by the agent to respond to the requests from the NMS.
Management Information Base (MIB)
The MIB is a collection of information organized hierarchically. These are accessed using a network management protocol such as SNMP. The MIB contains the definitions of various types of network information that can be retrieved from managed devices. Each piece of information in the MIB is identified by a unique identifier known as an Object Identifier (OID).
Object Identifiers (OIDs)
OIDs are organized in a hierarchical namespace. The hierarchy can be represented as a tree with a root at the top. The different levels of the tree are assigned by different organizations. The root of the tree contains OIDs like 1 (ISO), 2 (ITU-T), and 3 (joint-iso-itu-t). Below the root, different branches represent different organizations. For example, under the ISO branch, the branch 1.3.6.1 represents the Internet.
SNMP Versions
SNMPv1: The initial version, which provides the basic features of SNMP but lacks robust security mechanisms.
SNMPv2c: An enhanced version that introduced GETBULK and INFORM operations, but still has limited security features.
SNMPv3: The latest version, which provides significant improvements in security, including message integrity, authentication, and encryption.
Security in SNMPv3
SNMPv3 addresses the security shortcomings of its predecessors with several key features:
Authentication: Ensures that the message is from a valid source. It uses algorithms like MD5 or SHA.
Encryption: Protects the contents of the SNMP message from being read by unauthorized entities. It uses protocols like DES or AES.
Message Integrity: Ensures that the message has not been tampered with during transmission.
SNMP Message Format
SNMP messages are encoded in a format known as Abstract Syntax Notation One (ASN.1). Each SNMP message consists of a version number, community string (in SNMPv1 and SNMPv2c), or a user-based security model (in SNMPv3), and a protocol data unit (PDU).
Protocol Data Units (PDUs)
PDUs are the fundamental units of communication in SNMP. Different types of PDUs correspond to different SNMP operations. For example, GET, SET, and RESPONSE PDUs correspond to their respective operations.
Advantages of SNMP
Simplicity: SNMP is relatively simple to understand and implement.
Scalability: It can manage networks of varying sizes, from small to very large.
Standardization: Being an Internet Standard protocol, it is supported by a wide range of devices and vendors.
Extensibility: New MIB modules can be added to accommodate new types of devices and data.
Challenges and Limitations of SNMP
Security: Earlier versions (SNMPv1 and SNMPv2c) have very basic security features, making them vulnerable to various attacks.
Performance: Due to its reliance on the UDP transport layer, SNMP can be less reliable in networks with high levels of congestion.
Scalability Issues: In very large networks, the polling mechanism can become burdensome.
Complexity in Configuration: Properly configuring SNMP to balance security and functionality can be challenging.
Use Cases of SNMP
Network Monitoring: Tracking the performance of network devices and interfaces, such as bandwidth usage, error rates, and uptime.
Fault Management: Detecting and responding to network faults by receiving TRAP or INFORM messages.
Configuration Management: Changing the configuration of network devices remotely using SET operations.
Security Management: Monitoring network devices for signs of security breaches and unusual activity.
Performance Management: Collecting data on network performance to identify bottlenecks and optimize traffic flows.
SNMP plays a crucial role in modern network management, providing a standardized method for monitoring and controlling network devices. Its simplicity, extensibility, and broad adoption make it an essential tool for network administrators. Despite its limitations, advancements in SNMPv3, particularly in terms of security, have ensured its continued relevance in the field of network management.
Understanding SNMP involves grasping its basic components, operations, and the role of MIBs and OIDs. While its earlier versions had notable security weaknesses, SNMPv3 has significantly enhanced its security features, making it more robust for use in today's complex network environments. As networks continue to grow in size and complexity, the role of SNMP as a fundamental network management protocol remains pivotal.